An Assessment of Selected Divisions of the National Institute of Standards and Technology Information Technology Laboratory: Fiscal Year 2024 (2025)
Chapter: 3 Applied Cybersecurity Division
3
Applied Cybersecurity Division
INTRODUCTION
The Applied Cybersecurity Division (ACD) of the Information Technology Laboratory (ITL) was established on October 1, 2015. ACD’s mission is to “implement practical cybersecurity and privacy through outreach and effective application of standards, guidelines, and best practices necessary for the U.S. to adopt cybersecurity and privacy capabilities” (Stine and Petersen 2024).
Outreach to industry, academia, government, and others is central to ACD’s work. An important part of the outreach is listening to the needs and desires of its stakeholders. This ensures that the division focuses on the most important problems and builds trust, leading to increased influence.
The division approaches the task of ensuring that standards and guidance are applied effectively primarily through the National Cybersecurity Center of Excellence (NCCoE), which is a collaborative hub for government, industry, and academia to work together on pressing cybersecurity and privacy issues. ACD also devotes significant resources to ensuring that National Institute of Standards and Technology (NIST) guidance and specifications on privacy and security are effective through their Cybersecurity and Privacy Frameworks programs. Other NCCoE programs include the development and study of 5G deployments, digital identities (including mobile driver’s licenses), election systems, and the transition to post-quantum cryptography.
Education and workforce needs are addressed through the National Initiative for Cybersecurity Education (now known simply as NICE). NICE is also effective in developing the job market for cybersecurity researchers and practitioners by promoting a common language for skills and learning.
The Internet of Things (IoT) is a fast-moving technology area with concomitant security risks. ACD is active in enabling the deployment of secure and privacy-sensitive IoT devices by developing guidelines and requirements for the procurement and use of IoT devices across the federal government. The NIST Cybersecurity for IoT team also works to harmonize guidance and requirements across the globe by working with European Union regulators.
Other ACD activities include education and support for small businesses to benefit from NIST specifications and guidance.
ACD is central to driving changes to cybersecurity standards and practice. The division advances standards and guidelines critical to protecting the cyber infrastructure of the public and private sectors. The goal is to drive greater adoption of viable and widely adopted cybersecurity standards. ACD meets a critical need in cybersecurity by educating the cybersecurity workforce. It enables national and international consensus using public and private partnerships. Notably, ACD advances the market position of U.S. companies; the U.S. industry derives enormous benefits from the efforts of ACD, ITL, and NIST. ACD is critical to developing and driving changes to cybersecurity standards in the United States and globally.
Not every project presented to the panel is discussed in this report. Only those projects about which the panel had comments are discussed.
ASSESSMENT OF TECHNICAL PROGRAMS
National Cybersecurity Center of Excellence
NCCoE operates a collaborative hub to engage industry, government agencies, and academic institutions to accelerate the adoption of cybersecurity technologies. With its collaborators, NCCoE prototypes cybersecurity solutions for profiled environments using commercially available technology configured according to standards and best practice guidelines. NCCoE’s cybersecurity prototype solutions (1) enable the assessment of the practicality of implemented standards and guidelines and (2) facilitate their improvement.
NCCoE is currently pursuing 21 projects in the areas of risk management, applied cryptography, trusted platforms, operational technology, digital identity, and emerging technologies. NCCoE is addressing challenging problems throughout its portfolio of practical cybersecurity projects. The panel was introduced to 6 of the 21 projects, which are reviewed here. A review of the non-NCCoE projects follows the NCCoE projects.
NCCoE Migration to Post-Quantum Cryptography Project
The publication of Shor’s algorithm in 1994 suggested that many of the then-current encryption algorithms would be easily breakable with the advent of working quantum computers. The development pace of quantum technologies since that time suggests that the development of working quantum systems may be only 1 or 2 decades away. Not only is this a threat to ongoing cryptographic methods, but it also poses a threat to encrypted communications and data that may be stolen and held by malicious actors until technology resistant to quantum code-breaking is available—that is, encrypted data may be valuable to malicious actors even if it is not decrypted for decades.
It is critical that users of cryptography protect important material (e.g., health records, financial systems, and valuable intellectual property) by switching to quantum-resistant methods as soon as possible, to be ready to protect current data against future attacks when (and if) workable quantum computing is available to break cryptography. However, it takes time to make such a switch: to identify all of the use cases that need to be changed; introduce workable, tested methods; and ensure compatibility among products. This process may take years to complete, especially in large commercial products and databases.
NIST began an effort in 2016 to define new quantum-resistant algorithms for cryptographic use. This has been conducted in an open, collaborative mode with experts around the world. Candidate standards were published in 2021, and the first standards were published this year. To prepare for the release of official standards, NCCoE established an effort to coordinate and facilitate the switchover to quantum-resistant cryptography. This has included work on documentation, discovery tools, process models, and metrics.
NCCoE 5G Security Standards and Applied Research and the Zero Trust Laboratory Project
ACD has collaborated with industry stakeholders and academic institutions to establish a laboratory to design cybersecurity solutions tailored to 5G. This project focuses on integrating advanced technologies such as Network Functions Virtualization and Software-Defined Networking. It emphasizes a holistic approach that combines these technologies with cloud-based security features outside the scope of the 3rd Generation Partnership Project 5G security architecture, resulting in a robust security reference architecture.
Key project areas include secure network architecture, secure software development, and advanced threat detection and response mechanisms. The project highlights zero-trust principles, ensuring continuous monitoring and verification of network components. It also addresses supply chain security, recommending practices such as using static and dynamic analysis tools to identify vulnerabilities and
implementing secure update mechanisms to protect software and hardware components. Advanced threat detection capabilities are a critical focus to analyze network traffic and detect anomalies in real time. By integrating these technologies with 5G core network functions such as the Access and Mobility Management Function and User Plane Function, the project enhances the network operator’s ability to respond to security incidents promptly.
Additionally, the project explores the security implications of network slicing, a key feature of 5G that allows multiple virtual networks to operate on shared physical infrastructure. It provides guidelines for isolating and securing individual network slices to prevent the lateral movement of threats and ensure data confidentiality and integrity.
The project collaborates with various industry partners, including Dell Technologies, Intel, and Nokia. These organizations contribute relevant capabilities and product components to build and validate the example solutions. The project’s standards engagements are also critical. The technical outputs and insights gained from ACD’s research efforts form the foundation for active participation and contributions to the development of next-generation (e.g., 6G) cellular security standards. This ensures that the knowledge and advancements made by the project influence and shape future security protocols and guidelines in the 5G domain.
NCCoE Zero Trust Project
The Zero Trust project is intended to establish practical and actionable guidelines for implementing zero-trust principles within enterprise environments. This project seeks to address the ever-changing cybersecurity landscape. Historically, cybersecurity has been based on perimeter defenses, keeping people out. This approach is no longer adequate to protect against ever more sophisticated threats. Zero-trust architecture fundamentally shifts the security paradigm by assuming that threats could exist both inside and outside the network, and therefore, every access request should be authenticated, authorized, and continuously validated.
The Zero Trust project is structured around a collaborative effort involving industry experts, government agencies, and academic institutions. This consortium seeks to develop reference architectures and implementable solutions that enterprises can use to enhance their cybersecurity posture. By leveraging existing technologies and integrating them into a cohesive framework, the project provides practical examples and use cases demonstrating the application of zero-trust principles. These include identity and access management, micro-segmentation, continuous monitoring, and analytics to detect and respond to anomalies.
A key component of the project is the creation of detailed practice guides that outline the steps required to implement zero-trust architecture in various scenarios. These guides cover the configuration of technologies such as multifactor authentication, endpoint security, encryption, and network infrastructure. By providing a comprehensive and modular approach, ACD seeks to make zero-trust adoption feasible for organizations of different sizes and sectors, addressing common challenges such as legacy systems integration and scalability.
NCCoE Mobile Driver’s License Project
The Mobile Driver’s License project is new and is currently seeking collaborators. The project team described their first proposed use case focused on the use of a mobile (digital) driver’s license in a “know your customer” process for a financial services institution. This project will deploy technologies involved in identity verification and authentication and will apply standards addressing credential syntax and semantics, credential presentation protocols and application programming interfaces, and identity management.
While the project will begin with use cases for a mobile driver’s license, the project team intends to expand the scope of the project in the future to evaluate the use of other forms of verifiable identity credentials, such as the World Wide Web Consortium’s Verifiable Credentials.
This project is important, is well thought through, and is a good use of NCCoE’s limited resources. The panel strongly agrees with the project team’s intent to expand the testbed and use cases to assess other forms of verifiable identity credentials.
NCCoE NIST Cybersecurity Framework Profiles Project
The Cybersecurity Framework 2.0 introduces Community Profiles, which provide tailored cybersecurity risk management guidance for groups of organizations with common priorities. Community Profiles serve as collective cybersecurity risk management guidance for communities organized around the Cybersecurity Framework’s common taxonomy. They differ from Organizational Profiles, which are not shared publicly. The ACD team offers a structured approach to creating these profiles, including a template and a life-cycle model. By following the appropriate life-cycle model and leveraging the shared expertise within communities, organizations can enhance their cybersecurity posture.
NCCoE Cybersecurity and Privacy for Genomic Data Processing Project
Low-cost genomic sequencing has led to the creation of huge amounts of data, which contributes to U.S. leadership in health care. Genomic data need to be collected into large data sets to provide optimal value, but this aggregation leads to significant security and privacy risks. Privacy risks include leaks of people’s data. Security risks include the disclosure of proprietary data sets to competitors. An extreme example of a threat would be the use of such data sets to develop bioweapons (as noted in the “Executive Order on Safe Secure and Trustworthy Development and Use of Artificial Intelligence” [White House 2023]).
ITL’s Cybersecurity and Privacy for Genomic Data Processing project is studying all aspects of genomic security and privacy, encompassing current practices, risk assessment, and developing novel leading-edge solutions for storing and processing genomic data while minimizing risks of leakage and subversion. This work was directed by Congress and is partly in support of the Executive Order mentioned earlier.
NCCoE Election Security Project
Voting is a keystone of our democracy. The nation depends on voting to be accessible to all voters, accurately tallied, and free from malicious interference. Voters must also have privacy in their ballots. Voting technology supports a wide variety of elections and ballot initiatives, from voting for town dogcatcher to voting for U.S. President, from local school board budgets to state constitutional amendments, and more. Furthermore, it is desirable to allow voting technologies to be produced by multiple vendors yet still meet all these conditions.
As a consequence of the Help America Vote Act (P.L. 107-252) in 2002, Voluntary Voting System Guidelines were developed. As threats from outside the country and within have been manifested in both the 2016 and 2020 national elections, the need for rigorous standards and testing has become even more critical. The Election Security project plays a key role in the development, evaluation, and update of the Voluntary Voting System Guidelines as well as related efforts, including guidance on accessible interfaces and physical security. As technology progresses and gaps are identified, ACD works with appropriate parties, including state Secretaries of State, the Department of Homeland Security, vendors, and the Election Assistance Commission to evolve practice and guidance.
Cybersecurity and Privacy Small Business Outreach and Engagement Project
The Cybersecurity and Privacy Small Business Outreach and Engagement Project is a NIST initiative arising from the NIST Small Business Cybersecurity Act (P.L. 115-236) charged with
“disseminat[ing] clear and concise resources to help small business concerns identify, assess, manage, and reduce their cybersecurity risks.” The program is relatively new and currently relatively small.
Small businesses range from organizations with sole proprietorship to those with roughly 500 employees (the exact classification depends on the sector). Small businesses rarely have dedicated information technology (IT) staff, which means that they generally do not have the requisite skills to benefit directly from NIST cybersecurity guidance. This NIST outreach helps small and medium-size businesses use NIST standards and guidance to manage their risks. Outreach and engagement are discussed in detail in the section “Effectiveness of Dissemination Efforts” below.
Privacy Engineering Program
ACD’s Privacy Engineering Program is charged with “Support[ing] the development of trustworthy information systems by applying measurement science and system engineering principles to the creation of frameworks, risk models, guidance, tools, and standards that protect privacy and, by extension, civil liberties.”1 An additional strategic goal is to position ITL and NIST overall as a leader in privacy engineering to ensure that the institute is well placed to influence future privacy-related standards and practices. The work is authorized by the National Institute of Standards and Technology Act (15 U.S.C. 271).
One of the central deliverables of the Privacy Engineering Program is the NIST Privacy Framework (discussed below). The Privacy Framework is highly impactful, and some of this impact is clearly owing to the research and evangelism of the larger Privacy Engineering Program. The team has also directly and indirectly guided the development of international standards, for example, with the International Organization for Standardization (ISO) and International Electrotechnical Commission standards.
Identity and Access Management Project
Digital identity schemes are proliferating rapidly in both the public and private sectors. Some states are issuing mobile driver’s licenses. In addition, the OpenID Foundation and the FIDO Alliance, among others, have defined schemes that are being adopted in nongovernmental settings. One of the interesting initiatives is the creation of consortia to validate and study the use of mobile driver’s licenses in government, health care, and financial settings. The use of mobile driver’s licenses in these settings demands attention to usability and privacy and will probably require the development of additional protocols and standards; some of these points are elaborated on in the section “NCCoE Mobile Driver’s License Project,” earlier.
The ACD Identity Program is a multidisciplinary team with expertise ranging from mathematicians and cryptographers to policy specialists who address the challenges of developing and implementing digital identities. The team conducts research, develops standards, and guides and enables the adoption of digital identities. These areas will be studied by building testbeds for multiple end-to-end use cases.
Cybersecurity and Privacy Frameworks
NIST’s Cybersecurity Framework was first released in 2014 to help organizations understand, reduce, and communicate about cybersecurity risk. The Cybersecurity Framework is widely used within organizations to enable nontechnical management and technical cybersecurity practitioners to assess and manage cybersecurity risks.
___________________
1 See NIST’s “Privacy Engineering Program” website at https://www.nist.gov/itl/applied-cybersecurity/privacy-engineering, accessed September 26, 2024.
NIST’s Privacy Framework was first released in 2020 to enable privacy engineering practices that help organizations protect the privacy of individuals. The Privacy Framework is structurally aligned with the Cybersecurity Framework and enables traceability for privacy protection activities to meet regulatory obligations. Organizations can use the two frameworks together to manage their cybersecurity and privacy risks. The ACD Privacy Engineering team is in the process of developing a Privacy Workforce Taxonomy consistent with the Privacy Framework to describe the tasks, knowledge, and skills needed within a workforce to manage privacy risk.
While the Privacy Framework is young, stakeholders have already indicated its value through their investments in crosswalks2 to various laws, regulations, and standards (e.g., to the European Union’s General Data Protection Regulation); translations of the Privacy Framework into other languages; and the development of profiles for different types of organizations.
NICE Workforce Framework for Cybersecurity
The NICE Workforce Framework for Cybersecurity, commonly known as the NICE Framework, was first released in 2012 as a pivotal tool to enhance cybersecurity capabilities within the federal workforce. Originally established under the Comprehensive National Cybersecurity Initiative in 2008, the scope of NICE was expanded in 2009 to encompass the private-sector workforce.
NICE’s mission is to energize, promote, and coordinate a robust community dedicated to advancing cybersecurity education, training, and workforce development. This mission has been pursued through collaboration with government, academia, and industry partners. NICE’s strategic plan is intended to provoke a national dialogue and guide actions to address the critical shortage of skilled cybersecurity professionals. The NICE Community Coordinating Council and the NICE Interagency Coordinating Council facilitate public–private collaboration and federal coordination on policy initiatives and strategic directions in this domain. To accomplish its mission, NICE
- Hosts an annual conference and expo
- Hosts an annual K–12 Cybersecurity Education Conference
- Hosts an annual Cybersecurity Career Week
- Conducts webinars
- Hosts a Federal Cybersecurity Workforce Summit and Webinar Series
- Manages Federal Information Security Educators, an organization that helps federal agencies strengthen their workers’ cybersecurity awareness, and runs training programs to that end
NIST Cybersecurity for the Internet of Things Program
The Cybersecurity for the Internet of Things (IoT) program supports the development and implementation of standards, guidelines, and tools aimed at enhancing the cybersecurity of IoT systems, products, and environments. This program collaborates with stakeholders across government, industry, academia, international bodies, and consumers to build trust and foster global innovation. NIST IR 8316, Internet of Things (IoT) Component Capability Model for Research Testbed (NIST 2020a), elaborates that IoT systems consist of networked components interacting with physical entities through sensors or actuators, distinguishing them from conventional IT systems, which do not interact directly with the physical world. NIST has further defined an IoT product in NIST IR 8425, Profile of the IoT Core Baseline for Consumer IoT Products (NIST 2022b), as comprising one or more IoT devices and related
___________________
2 From NIST’s Privacy Framework website, “These crosswalks are intended to help organizations to understand which Privacy Framework Functions, Categories, and Subcategories may be most relevant to addressing the provisions of the source document. Organizations should not assume implementation of these Privacy Framework activities or outcomes means that they have met the provisions of the source document. There may be other activities that organizations need to undertake” (NIST 2024a).
components such as networking hardware, companion application software, and backend services. These products can form complex IoT systems that serve consumer needs. The publication is intended to help manufacturers produce more secure IoT products and assist organizations in securing those products.
The IoT program encompasses a broad spectrum of activities designed to ensure comprehensive and inclusive input. These activities include leveraging existing NIST guidance, conducting landscape reviews, considering publicly available information on past events, and consulting informally with academic, civil society, and industry experts. Public interactions are facilitated through numerous in-person and virtual workshops, garnering significant participation, and extensive engagement with almost 2,000 public comments across draft and final publications. ACD IoT program staff members also actively participate in standards development, bilateral and multilateral governmental discussions, and present findings at domestic and international conferences. Key stakeholders actively involved in NIST’s IoT program include the following:
- U.S. government agencies such as the Food and Drug Administration, Department of Energy, and Cybersecurity and Infrastructure Security Agency
- Various NIST organizations
- International government agencies such as the EU Commission and the European Union Agency for Cybersecurity (i.e., ENISA)
- Standards development organizations such as ISO and the International Electrotechnical Commission
- Academic institutions such as the Massachusetts Institute of Technology and Carnegie Mellon University
- Civil society organizations such as the Center for Democracy and Technology
- Industry groups such as the U.S. Chamber of Commerce and the Information Technology Institute
Accomplishments
Small Business Cybersecurity and Privacy Outreach Program
To date, this program has focused on coordinating NIST’s cybersecurity efforts with small and medium-size business-related programs and relationships across the federal government, building relationships with partners, and educating small and medium-size businesses about NIST’s cybersecurity resources. The community-building and education program creates tailored web resources—offering guidance by sector and topic—and webinars. Web metrics—the number of page views, downloads, and webinar attendees—indicate that the program has started well.
National Cybersecurity Center of Excellence
NCCoE “How-To Guides” document the process of installing and configuring the commercial products in one or more NCCoE project implementations. To ensure that the setup process for the exemplar cybersecurity solutions is replicable, the guides provide detailed configuration instructions, including screenshots of setup windows, the options selected in pull-down menus, and the sequence of button clicks.
Migration to Post-Quantum Cryptography Project
This program appears to be managed well and is making good progress. Draft documents providing guidance were published at the end of 2023. Laboratory demonstrations of performance and interoperability tools were performed this year. The effort has also resulted in the formation of a large, active, and appropriate working group of more than 1,600 members from both industry and government.
Publications and presentations appear to be attracting community engagement. The effort to date is commendable and the topic is potentially critical. The plans for future steps appear reasonable, and it is important that appropriate resources be applied to this effort maintain and add appropriate resources to maintain progress.
5G Security Standards and Applied Research and the Zero Trust Laboratory Project
The ACD 5G Cybersecurity Project has produced a range of publications and has built a 5G testbed to guide the management of 5G cybersecurity risks. Notably, volumes of NIST SP 1800-33 (draft), 5G Cybersecurity NIST SP 1800-33 Practice Guide Preliminary Draft (NIST 2021a), and various cybersecurity white papers offer detailed guidance. Additionally, ACD provides recorded demonstrations and informational sessions to further educate stakeholders on 5G security best practices.
NIST Cybersecurity Framework Profiles Project
This project has put out several Community Profiles. A few examples of Community Profiles that illustrate their application across different sectors and use cases are
- Cybersecurity Framework 1.0 Community Profiles: Manufacturing, Maritime Specific, Communications Sector, among others.
- Cybersecurity Framework 1.1 Community Profiles: Manufacturing, Election Infrastructure, Ransomware Risk Management, Liquefied Natural Gas, Hybrid Satellite Networks, Genomic Data, Electric Vehicle Charging, Smart Grid, and more.
- Cybersecurity Framework 2.0 Community Profiles: Incident Response Recommendations, Cyber Risk Institute Profile for the Financial Sector.
As of this writing, the guide is currently under review, with public comments being analyzed. Additionally, the panel noted that they need to continuously develop additional community profiles, engage new and existing communities, expand content in the Framework Resource Center, and refine the community profiles template.
Cybersecurity and Privacy for Genomic Data Processing Project
The starting point for this work is understanding and quantifying risk. Many of the risks are common to other data sets, but there are enough unique challenges to warrant the development of sector-specific evaluation metrics. ACD approached this by developing testbeds and domain-specific cybersecurity frameworks and profiles. Risk quantification is guided by NIST IR 8477, Mapping Relationships Between Documentary Standards, Regulations, Frameworks, and Guidelines: Developing Cybersecurity and Privacy Concept Mappings (NIST 2024b). This report defines security objectives (e.g., “Preserve Privacy of Donors”) and details the security principles and best practices that can contribute to the security mission. ACD collaborated with health and genomics experts in this work. The relevant experts in both cybersecurity and genomics contributed beneficially, and community feedback on the value of this work has been positive.
Election Security Project
Voting and vote counting have become highly politicized topics. The NCCoE efforts in this area have kept focused on verifiable and understandable technical guidance. Wider understanding and acceptance of this guidance, and testing real systems against it, is one way to quiet some of the suspicions and disagreements in this arena.
ITL has played a key role in the development, evaluation, and update of guidelines to secure elections, as well as in related efforts including guidance on accessible interfaces and physical security. As technology has progressed and gaps have been identified, ACD has worked with the appropriate
parties, including state Secretaries of State, the Department of Homeland Security, technology vendors, and the Election Assistance Commission to continually develop practice and guidance in response to new threats and challenges. In particular, ACD has supported the development of the Voluntary Voting System Guideline 2.0 and the promotion of fundamental ideas such as software independence and risk-limiting audits. Its Voting Technology Series of guidance documents is particularly valuable to the community (NIST 2024c). ACD is to be commended for its careful and highly valuable work in this topic area. It is vitally important that this be an ongoing effort, maintained at a level appropriate for the needs involved.
Privacy Engineering Program
One of the central deliverables of the Privacy Engineering Program is the NIST Privacy Framework, which is described in more detail above. In addition to this foundational work, the Privacy Engineering team has developed a collection of privacy engineering–related tools and a collaboration space. These resources allow NIST and other expert practitioners to study topics such as disassociability (using differential privacy and other techniques) and assessing privacy risks. The team has also sponsored competitions to advance the understanding and adoption of privacy-enhancing technologies. One recent focus is maintaining privacy in federated machine learning. Also of note is the Privacy Risk Assessment Methodology, which drastically reduces the time that it takes to discover and quantify a privacy risk. The Privacy Engineering Program has advanced and promoted the state of the art in privacy in differential privacy (adding statistical noise) and federated learning (learning without actually sharing data).
Identity Program
A foundational component of the Identity Program is the NIST 800-63 family of guidelines that address the management and use of digital identities. These special publications are directed toward federal agencies’ use of digital identities, but they are applicable to nongovernmental use as well.
These special publications are highly influential in how digital identities are being managed and adopted. Elsewhere in this report, it is argued that simple engagement counts are a poor indicator of NIST’s societal impact, but here it bears noting that there were approximately 3,800 comments during the public comment period for the fourth revision, with 70 percent coming from the private sector—a clear indicator of the importance of this work.
Identity and Access Management Project
An important aspect of this work is coordinating U.S. efforts with the EU approach to digital identity codified in eIDAS regulation.3 This mapping effort is particularly important because the European Union is pursuing a mandatory regulatory approach, while the United States mainly provides noncompulsory guidance. The draft EU–U.S. TTC WG-1 Digital Identity Mapping Exercise Report (NIST 2023) will help ensure that the ecosystems are aligned and hopefully interoperable for some scenarios, something that is important for U.S. industries and technologies to compete globally.
ACD’s identity program is having an outsized impact, both within the federal government (e.g., the Social Security Administration, Internal Revenue Service, and Department of Health and Human Services), by the states (e.g., mobile driver’s licenses), and in the private sector (perhaps a billion users protected by phishing-resistant authenticators, according to Google and the FIDO Alliance).
NICE Workforce Framework for Cybersecurity
Internationally recognized, the NICE Framework has been adopted and translated by organizations worldwide, including those in the United Kingdom, Canada, and Australia, demonstrating
___________________
3 See the European Commission’s website “eIDAS Regulation” at https://digitalstrategy.ec.europa.eu/en/policies/eidas-regulation, accessed August 21, 2024.
its global influence. NICE is currently exploring the development of industry-specific profiles to tailor the framework to various sectors, enhancing its applicability and flexibility. Also, the NICE Framework Resource Center offers tools, guides, and resources to support the implementation and use of the framework, reinforcing its role as a critical tool for maintaining national cybersecurity. Through these efforts, NICE continues to lead in promoting cybersecurity education and workforce development, coordinating NIST cross-functional teams, interagency coordination, stakeholder engagement, and international harmonization. There have been approximately 1,644 downloads of NICE Framework v1.0.0 and more than 20,000 views by nearly 13,000 users of the NICE Framework Resource Center landing page since March 2024. In addition, there has been a 40 percent growth in members of the NICE Framework Users Group in FY 2024.
NIST Cybersecurity for IoT Program
Notable accomplishments of the NIST Cybersecurity for IoT program include receiving the World Innovation, Technology, and Services Alliance Chairman’s Award in 2023. NIST’s IoT definition from NIST IR 8259, Foundational Cybersecurity Activities for IoT Device Manufacturers (NIST 2020a), was cited in the IoT Cybersecurity Improvement Act (P.L. 116-207). Since 2017, this program’s publication suite has seen more than 275,000 downloads with several publications translated into Spanish and Portuguese.
Publications such as NIST SP 800-213/-213A, IoT Device Cybersecurity Guidance for the Federal Government: Establishing IoT Device Cybersecurity Requirements (NIST 2021b), form the basis for the Office of Management and Budget’s Federal Information Security Management Act guidance on IoT, and the NIST Consumer Profile underpins the Federal Communications Commission U.S. Cyber Trust Mark criteria. NIST’s IoT cybersecurity research has been recognized as an inspiration for the EU Cyber Resilience Act critical criteria and recommended by the Federal Trade Commission for IoT product manufacturers. Additionally, California amended its IoT Security Law to provide a safe harbor for connected device manufacturers complying with NIST criteria. International standards ISO 27402 and American National Standards Institute-2088 were based on NIST IR 8259, Foundational Cybersecurity Activities for IoT Device Manufacturers (NIST 2022a), and American National Standards Institute/Consumer Technology Association 2119, “Framework for Evaluation of a Cybersecurity Scheme,” currently in development, is based on NIST IR 8425, Profile of the IoT Core Baseline for Consumer IoT Products (NIST 2022b).
Overall, the NIST Cybersecurity for IoT Program plays a crucial role in improving the cybersecurity of IoT systems and devices. Its guidance publications, engagement with stakeholders, and impact on legislation and industry practices demonstrate its effectiveness in addressing the unique challenges of IoT cybersecurity. By fostering trust and enabling innovation, the program contributes to a more secure and resilient IoT ecosystem.
Opportunities and Challenges
There has been recent revolutionary progress in foundational artificial intelligence (AI) and its application. It is expected that AI will impact most aspects of life and commerce in the next few years. However, the impact of AI on the field of computer security is currently unclear. AI can be used by both attackers and defenders, and new AI-powered products and services will introduce new risks that are currently not understood. There are also increased privacy concerns related to the data used to train AI systems. It is vitally important that the responsible use of AI be explored and addressed. At the time of writing, the panel does not have specific recommendations for new AI-focused projects or new AI-related workstreams on existing projects but believe that developing staffing, equipment, and expertise in AI will be critical for ACD to be effective in the next decade.
Cutting-edge research, model training, and inference all demand a significant investment in hardware, data and software, operations (e.g., power), and staff. Developing these capabilities will be expensive, and talent will be recruited only if the facilities are of a high caliber.
Recommendation 3-1: Existing and new Applied Cybersecurity Division projects should include the study of the security, privacy, and responsible uses of artificial intelligence (AI), including the security and privacy characteristics of AI systems.
Small Business Cybersecurity and Privacy Outreach Program
It is particularly challenging for small non-IT-sector businesses—approximately 80 percent of U.S. small businesses are single-proprietorships—to apply ACD guidance. Much of the available guidance designed for small businesses—provided by organizations including the Department of Homeland Security Cybersecurity and Infrastructure Security Agency, the Small Business Administration (SBA), and the Federal Trade Commission—assumes organizational roles that do not exist in single proprietorships or partnerships. It would be wasteful for ACD to expend its limited resources to develop materials that are somewhat duplicative of existing federal resources and do little to help the many tiny businesses that are underprotected from cyberattacks. Also, the gap between the estimated number of small businesses—approximately 30 million—and the size of the current community—approximately 1,000 attendees for a webinar—is considerable.
In contrast, by developing new, streamlined guidance specifically tailored for businesses that employ at most five individuals, ACD could assist the large majority of the small business community that is currently underserved by existing information sources. For example, ACD could partner with the SBA to develop and host training videos, checklists, and other materials that target this community. The SBA has regional centers that host events, which could include cybersecurity outreach and education. ACD’s educational reach could be extended by focusing on training the SBA trainers in SBA regional communities.
Recommendation 3-2: The Applied Cybersecurity Division (ACD) should focus on the development of new, specialized cybersecurity guidance for single proprietor or partnership businesses with only a few employees. It should partner with the Small Business Association to develop training materials such as videos and checklists and support regional outreach to enable ACD to have a broader impact within the limited resources available to the program.
National Cybersecurity Center of Excellence
Whenever possible, it is advisable that NCCoE’s individual projects use Configuration as Code tools—such as Ansible, Puppet, Chef, and SaltStack—or Infrastructure as Code tools such as Terraform to record project technology configurations and setup steps. Using such tools will allow the creation of configuration manifests that can succinctly capture the technical steps used to deploy and configure technologies and enable automated, replicable deployment of specific cybersecurity solutions. Such manifests are also amenable to analysis by automated configuration assessment tools, which can highlight configuration conflicts or security issues. Publication of configuration manifests to a code repository such as GitHub could enable NCCoE teams to more concisely express technical deployment details and enable a clearer understanding and assessment of the applicability and improved replicability of NCCoE engineering work.
5G Security Standards and Applied Research and the Zero Trust Laboratory
Despite its strengths, this effort can be improved by enhancing scalability and ensuring interoperability among different vendors’ equipment and security solutions instead of focusing on a single vendor stack.
Zero Trust Project
To further improve the Zero Trust project, several enhancements can be considered. First, enhancing interoperability with a wider range of legacy systems and emerging technologies than is currently the case can facilitate smoother transitions. Second, expanding use cases and scenarios in practice guides can offer more tailored solutions, addressing unique challenges in various sectors. Third, incorporating more automation into zero-trust implementations can help manage security policies and responses more efficiently. Last, developing comprehensive training programs for IT staff and end users seeking to deploy zero-trust solutions can ensure better implementation and adherence to security protocols such as closer collaborations with parallel initiatives such as NICE.
NCCoE Mobile Driver’s License
It would be useful for the project team to consider further expanding the testbed and use cases to address trade credentials. International import and export currently rely on paper-based credentials (or digital representations from scanned paper) that document the characteristics and provenance of products and their components for manufacturers, shippers, customers, and government regulators. Verifiable digital credentials for trade have the potential to both improve security and streamline international import and export processes. Security requirements for trade credentials are likely to differ from those for digital identities. Stringent technical privacy requirements for digital identities, especially to prevent the tracking of individuals, are almost inverted for product provenance credentials: tracking the provenance of product components and aggregation of production certifications (e.g., environmental and anti-forced labor) are necessary. The set of potential industry, government agencies, and other institutional collaborators for digital identity projects such as the current Mobile Driver’s License project and future projects involving other verifiable identity credentials is likely to differ greatly from those that will participate in projects involving trade credentials.
NIST Cybersecurity Framework Profiles
Considerable effort has gone into making the Cybersecurity Framework Profiles. In theory, these profiles should see widespread use. However, no plan to evaluate the adoption and effectiveness of these profiles was presented. Such a plan, or plans, is important to understand how effective the division is in helping users implement cybersecurity approaches and in guiding future efforts along these lines. The standard period for public comment will result in self-selected respondents who may not adequately represent the target demographic. An active effort will yield better results. ITL’s Statistical Engineering Division might be able to help with this.
Recommendation 3-3: The Applied Cybersecurity Division should conduct a study of the target audiences for its Cybersecurity Framework Profiles to determine if they are being used to full effect, and to determine if their content and format are appropriate for the intended audiences. The Statistical Engineering Division should be consulted on this. Future profiles and the allocation of resources to support their development should be informed by this study.
Cybersecurity and Privacy for Genomic Data Processing
One of the particularly interesting challenges in genomic data sets is that competitive threats in combination with ethical and regulatory considerations lead to data sets that are typically fragmented across different companies, research laboratories, and hospitals. There is a widespread belief that aggregating these data sets for analysis will lead to deeper insights, but the risks of data theft or disclosure make this undesirable. Privacy-enhancing technologies offer mechanisms that allow computation across different data sets with limited and controlled disclosure of the underlying data itself. ACD is exploring the use of privacy-preserving federated machine learning to address this challenge. This approach certainly has merit. Alternative approaches, perhaps based on confidential computing, could also be
explored to understand the strengths and weaknesses of each. ACD is to be commended for this important work and the panel fully supports ACD’s assessment that the techniques being developed in this area are applicable to many other scenarios outside genomics and health care.
Identity and Access Management
ACD could invest more into the study of the robustness of various implementations of digital identities, particularly how systemic risks can be mitigated, and of identity ecosystems that can be rebuilt in the case of a large and effective cyberattack. As digital identities are used for more scenarios, the attractiveness of the digital identity ecosystems as cyber-targets will grow. As identity is the basis for almost all other services, it is particularly critical that these ecosystems are resilient and recoverable.
Recommendation 3-4: The Applied Cybersecurity Division should supplement its work on digital identities with a study of the implications and remediation of a large-scale cyberattack on modern identity systems, such as what might arise from vulnerabilities in widely used desktop or mobile operating systems.
Privacy Framework
The panel encourages the Privacy Framework team to emphasize investment-based impact metrics for different stakeholder communities. For example, a law firm with a large practice in digital assets and data management invested significant effort to develop a crosswalk between the Privacy Framework and the California Consumer Privacy Act of 2018. Such stakeholder investment is a strong indicator of the value of the Privacy Framework to the legal community.
ASSESSMENT OF SCIENTIFIC EXPERTISE
ACD reports FY 2023 staffing levels of 184 associates, 44 scientists, and 2 support staff.4 Figure 3-1 shows the ACD staff levels from FY 2015 through FY 2024. It can be seen that permanent ACD staff levels have fluctuated but appear to have been fairly level since FY 2020. The number of associates, however, has shown significant change, with a dramatic increase in FY 2016, rising to a maximum in FY 2022, and decreasing after that. While ACD reports 184 associates in FY 2023, it can be seen that there are significantly fewer associates in FY 2024.
ACD did not provide detailed information on staff honors and awards. They reported that their staff have won nine internal and external awards. However, awards and honors are not the only measures of quality. Based on interactions with the staff over the course of the meeting, it is clear that the overall expertise of the ACD staff is excellent.
Furthermore, ACD staffs its projects with scientific experts from across ITL and NIST more broadly and collaborates with other national and international government agencies, industry, and academic institutions. The resulting project teams create a world-class workforce of internal and external subject-matter experts to advance standards and guidelines. The depth and breadth of the researchers accelerate impactful outcomes for the broader cybersecurity community.
___________________
4 Associates are not NIST employees. They are outside researchers, both foreign and domestic, who collaborate with NIST researchers.
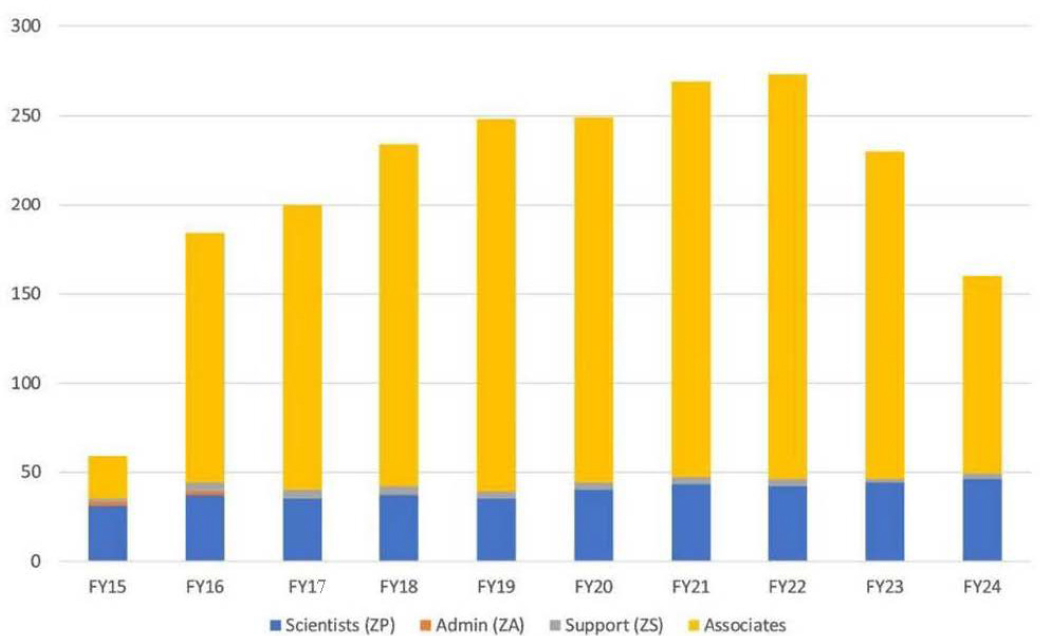
SOURCE: Courtesy of NIST Information Technology Laboratory.
BUDGET, FACILITIES, EQUIPMENT, AND HUMAN RESOURCES
ACD’s FY 2024 budget is $62 million. Figure 3-2 shows ACD budget levels and trends from FY 2016 through FY 2024. The budget has three major components: congressional scientific and technical research services (STRS) appropriations, internal funding competitions such as the Innovations in Measurement Science internal grant competitions, and work done for other federal agencies.
ACD is an excellent steward of funds: it engages creative and effective strategies to staff critical projects. It is notable that while the ITL budget has increased by approximately 20 percent between FY 2016 and FY 2024 (staff growth has not matched budget growth because labor costs have grown), it has not kept pace with the growth of the IT sector. By some measures, IT sector revenues have doubled since 2016.5 Other business sectors are increasingly dependent on advances in IT. As IT powers more and more businesses, sectors, and governmental functions, the attractiveness of IT systems as cybertargets grows commensurately. ITL, and NIST broadly, is foundational to how the nation secures its infrastructure, and the panel believes that greater investment in ITL would lead to increased growth and stability of the IT sector and the businesses it powers, reduced cybercrime, and decreased risk of catastrophic black-swan events.
In the course of the meeting, the panel toured some of the laboratories and other facilities in NCCoE and on the Gaithersburg, Maryland, campus. Overall, they are adequate to support the needs of ACD and ITL more broadly.
___________________
5 See Statista’s “IT Services—United States” website at https://www.statista.com/outlook/tmo/itservices/united-states, accessed August 21, 2024.
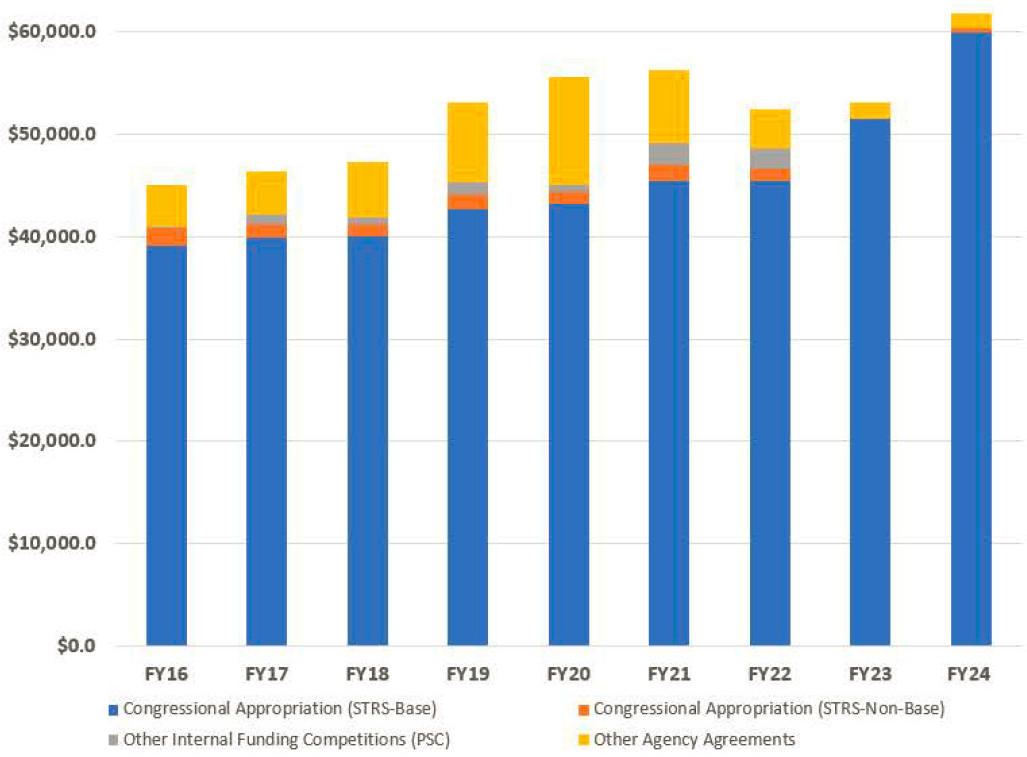
NOTE: PSC, Public Safety Communications; STRS, scientific and technical research services.
SOURCE: Courtesy of NIST Information Technology Laboratory.
The risk of losing key staff and expertise, particularly because of the laboratory’s current demographics, is concerning. A large proportion of ACD staff is eligible for retirement within the next 10 years. Specifically,
- 26.1 percent are eligible to retire now.
- 6.5 percent will be eligible in 3 years.
- 2.2 percent will be eligible in 5 years.
- 8.7 percent will be eligible in 10 years.
- 56.5 percent will be eligible beyond 10 years.
Among the nation’s senior IT and computer security engineers, there is a strong appetite for engaging in unpaid community service to “make a difference.” The volunteers on this panel are a good example of this. This includes senior cybersecurity engineers, not only researchers. The panel advises that ACD explore creative, and hopefully inexpensive, approaches to tapping into this underused resource. This might include developing visiting engineer programs or collaborations in addition to NIST’s existing visiting researcher programs.
Recommendation 3-5: The Applied Cybersecurity Division (ACD) should explore innovative approaches to staff augmentation and retention. ACD should also develop programs to engage senior volunteer cybersecurity research and engineering talent to serve the nation through its programs and activities.
EFFECTIVENESS OF DISSEMINATION EFFORTS
A key part of ACD’s mission is to ensure that NIST standards and guidance are practical and effective. ACD attributes part of its effectiveness to the fact its staff “listen, lead, and are trusted.” This aphorism captures an important feedback loop: for ACD to be effective, it must provide high-quality and useful standards and guidance. This requires experts—from both within and outside NIST—to volunteer their time, which they will do only if they believe that they can influence NIST’s work product and that the results are valuable and important. ACD staff have built healthy and active communities of users and experts for most of the projects assessed in this report. The open and collaborative approach taken by the staff of ACD has led to these successes.
ACD staff also noted at the meeting that “We work quietly behind the scenes, ensuring the things you rely on daily are safe, reliable, and compatible. Think of us as the invisible force powering everything from your smartphone to the bridges you cross.” The panel supports this assessment but believes that more visibility, and perhaps more importantly, better quantification of the impact on U.S. competitiveness, would result in resources commensurate with the size of the existing challenges and opportunities.
The panelists from the private sector stress how important and influential NIST standards and guidance are to their businesses. Adherence to NIST standards reduces risks, reduces costs, and increases competitiveness far beyond the measurable impacts that NIST cited. NIST is a crown jewel of our national laboratories for IT.
ACD provided the following dissemination metrics for FY 2021 through FY 2023:
- 624,000 total ACD publication downloads
- 5.7 million visits to the Cybersecurity Framework website, the most-visited site in NIST
- Approximately 75,000 followers on the @NISTcyber X account, nearly double those in FY 2021
- 54 publications, including special publications (in the 800 and 1800 series among others), interagency reports, internal reports, and white papers
- 25 in FY 2021
- 19 in FY 2022
- 10 in FY 2023
- 45 blogs, promoted via GovDelivery and X, with approximately 95,000 views
- More than 15,000 registrants for events, workshops, and conferences
ACD’s efforts to engage stakeholders and monitor the impact of individual ACD projects are impressive.
ACD’s methods for continuous and periodic feedback, broad stakeholder engagement, and comprehensive workshops promote successful collaboration of scientific experts. ACD actively hosts webinars and meetings to update the ecosystem on project status. The team also presents at and participates in industry conferences and working groups to foster collaboration. Furthermore, ACD engages with various international governments to discuss and develop strategies for managing cybersecurity risks. However, the impact metrics are inconsistent and somewhat lacking. The size of a community as measured by webinar participation or download counts is interesting but is not a fair or complete measure of the actual value of ACD’s outreach and dissemination. In general, ACD projects are
undervalued and their impact underappreciated. ACD needs to develop improved metrics for individual projects that focus on the quality and magnitude of their impact.
Note that all who participate in communities of practice are self-selected. To truly assess the impact on the intended communities, ACD needs to randomly select intended stakeholders from whom to solicit input. It is understood that there are constraints on ACD’s ability to solicit information about stakeholder use and impact, such as Office of Management and Budget mandates regarding conducting surveys, but the panel encourage the development of metrics that go beyond counting the number of downloads.
One source for ideas might be the open-source community and how they measure the impact and use of an open-source project. For instance, it might be interesting and useful to track the quantity and frequency of external contributions to ACD documents and the number of issues reported by adopters and implementers. More ideas can be found in the section “What to Track” on the Linux Foundation website, Measuring Your Open Source Program’s Success.6
For NCCoE projects, one metric of industry value might be the percentage of collaborating companies that are repeat participants, participating in two or more NCCoE projects. Such a measure might apply differently to small, narrowly focused start-ups than to large, established technology companies.
Recommendation 3-6: The Applied Cybersecurity Division should develop impact metrics for individual projects and apply them uniformly. Metrics should include economic benefits for adopters and quantification of risk reduction, where possible. Useful ideas may be found, for example, through the open-source community and the Linux Foundation.
PLANNING
As noted earlier, the panel has some concerns that adequate resources be provided to ACD for its important work. New projects are being mandated by legislation and executive orders, and AI, cloud computing, complex supply chains, and other advancements are profoundly changing the practice of and science of computer security.
ACD also faces the potential for significant retirements leading to questions about there being adequate experience to support ACD’s work in the future. The panel is concerned that at the current level of staffing and the rate at which new projects are mandated, there is a risk of staff and expertise being spread too thin, leading to reduced value and impact from ACD’s work.
Recommendation 3-7: The Applied Cybersecurity Division (ACD) should develop and share a strategic vision for how projects are selected and managed in ACD to balance the demands on the division with the available resources and prevent the loss of value and impact from being overstretched.
REFERENCES
NIST (National Institute of Standards and Technology). 2020a. Foundational Cybersecurity Activities for IoT Device Manufacturers. IR 8259. May. https://csrc.nist.gov/pubs/ir/8259/final.
NIST. 2020b. Internet of Things (IoT) Component Capability Model for Research Testbed. IR 8316. September. https://nvlpubs.nist.gov/nistpubs/ir/2020/NIST.IR.8316.pdf.
___________________
6 See the Linux Foundation’s Open Source Guide “Measuring Your Open Source Program’s Success,” at https://www.linuxfoundation.org/resources/open-source-guides/measuring-your-open-source-program-success, accessed August 21, 2024.
NIST. 2021a. 5G Cybersecurity NIST SP 1800-33 Practice Guide Preliminary Draft. February 1. https://www.nccoe.nist.gov/publications/practice-guide/5g-cybersecurity-nist-sp-1800-33practice-guide-preliminary-draft.
NIST. 2021b. IoT Device Cybersecurity Guidance for the Federal Government: Establishing IoT Device Cybersecurity Requirements. SP 800-213. November. https://csrc.nist.gov/pubs/sp/800/213/final.
NIST. 2022a. Foundational Cybersecurity Activities for IoT Device Manufacturers. IR 8259. May. https://csrc.nist.gov/pubs/ir/8259/final.
NIST. 2022b. Profile of the IoT Core Baseline for Consumer IoT Products. IR 8425. September. https://nvlpubs.nist.gov/nistpubs/ir/2022/NIST.IR.8425.pdf.
NIST. 2023. EU-US TTC WG-1 Digital Identity Mapping Exercise Report. Updated December 22. https://www.nist.gov/identity-access-management/eu-us-ttc-wg-1-digital-identity-mappingexercise-report.
NIST. 2024a. “Crosswalks.” Updated May 8. https://www.nist.gov/privacy-framework/resourcerepository/browse/crosswalks.
NIST. 2024b. Mapping Relationships Between Documentary Standards, Regulations, Frameworks, and Guidelines: Developing Cybersecurity and Privacy Concept Mappings. IR 8477. February. https://csrc.nist.gov/pubs/ir/8477/final.
NIST. 2024c. “NIST Technical Series Publication List: VTS.” Updated March 13. https://pages.nist.gov/NIST-Tech-Pubs/VTS.html.
Stine, K., and R. Petersen. 2024. “2024 NASEM Review: Applied Cybersecurity Division.” Presentation to the panel. National Cybersecurity Center of Excellence. June 4.
White House. 2023. “Executive Order on the Safe, Secure, and Trustworthy Development and Use of Artificial Intelligence.” October 30. https://www.whitehouse.gov/briefing-room/presidentialactions/2023/10/30/executive-order-on-the-safe-secure-and-trustworthy-development-and-use-ofartificial-intelligence.

















