National Science, Technology, and Security Roundtable Capstone: Proceedings of a Workshop (2025)
Chapter: 9 Potential Near- and Long-Term Responses on Research Security
9
Potential Near- and Long-Term Responses on Research Security
Kathryn A. Moler (Stanford University) moderated the workshop’s final panel, a session that considered future responses for meeting the goal of securing scientific research while preserving openness in the research system of the United States. Moler began the session by summarizing key themes from the preceding workshop sessions: the importance of providing appropriate resources for both addressing research security and maintaining U.S. research preeminence; the need to properly assess and categorize research that needs protection; the importance of expertise to support being able to make security decisions case by case; the need for a strong talent development program within the United States; thinking about talent as a supply chain issue; the importance of shared values in conducting research; and the appropriate response in instances where shared values are not present.
Kelvin Droegemeier (University of Illinois Urbana-Champaign), former director of the White House Office of Science and Technology Policy, said that there has been a lot of progress on research security over the last several years, commending the National Science, Technology, and Security Roundtable (NSTSR) and its communications efforts.
Droegemeier said that U.S. global competitiveness is proportional to our capabilities and investments, and inversely proportional to threats to (and interference with) our values. We should “lead with our values,” which are the principles by which we operate. Values must not be compromised, as they constitute a necessary and an inseparable dimension of research. These values can be returned to when disagreement or confusion
arises. For the United States, national and research values include honesty, integrity, transparency, accountability, openness, collaboration, fairness, merit-based competition, objectivity, and reciprocity (see Figure 9-1). The United States can live up to our values by strengthening and actively promoting messaging on our values and holding continuous conversation on values to deepen cultural norms; linking values to research security measures and open science; and highlighting values as a benefit to performing research in the United States and in international collaborations.
Droegemeier said that we should “not play to not lose.” The United States has taken a much more defensive position that stems, in part, from intentional efforts by adversaries to force the United States to expend resources on the challenges of research security. We must also “untie our hands” by reducing regulations. Currently, nearly 50 percent of researcher time is spent on administrative activities. The Office of Management and Budget and its Office of Information and Regulatory Affairs should work with nongovernmental organizations such as the Council on Government Relations, Association of American Universities, Association of Public and Land-grant Universities, and Federal Demonstration Partnership to identify specific research regulations and policies that can be changed or suspended under executive order to reduce administrative burdens on researchers.
Droegemeier said that it is critical that the United States invest in talent development on a national level and cited as precedent for this the G.I. Bill (P.L. 78-346), National Defense Education Act of 1958 (NDEA; P.L. 85-864), and Post 9/11 Veterans Educational Assistance Act of 2008 (P.L. 110-252). In addition, the United States must look beyond the visible horizon and develop a comprehensive, multisector, whole-of-nation, 25-year science and technology (S&T) vision for the country. There are inherent challenges to this, for example: the United States’ decentralized, multisector structure challenges planning and coordination; responsibility for agency budgets and priorities are spread across Congress; and interagency collaboration often depends on intangibles (e.g., the personalities involved or who is working to make things happen). However, short-term thinking is no longer a viable option.
Droegemeier called upon the National Academies of Sciences, Engineering, and Medicine to take a leadership role in crafting a national S&T security strategy. It is challenging for the executive branch, the White House, Congress, a laboratory, a university, or a university consortium to lead on this. The National Academies is in the best position to lead this

SOURCE: Kelvin Droegemeier, July 17, 2024.
effort because it is viewed as having effective convening ability and a neutral status. It would be important to have co-chairs who are stakeholders to help gain buy-in from affected communities.
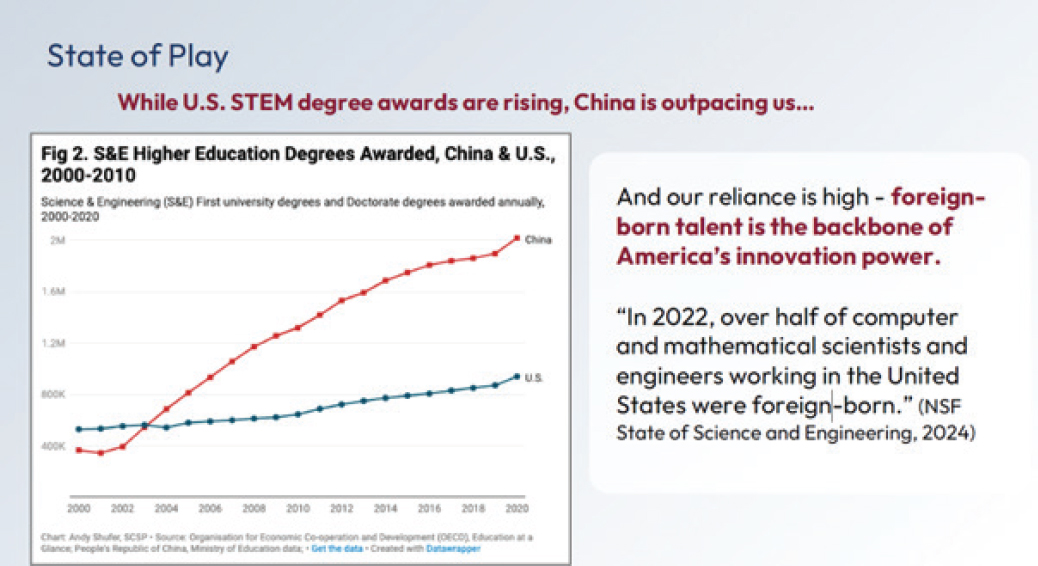
Diana Gehlhaus (Special Competitive Studies Project) spoke about growing and cultivating the U.S. science, technology, engineering, and mathematics (STEM) workforce. Leaks in the talent pipeline occur consistently throughout the pipeline, starting at kindergarten and continuing through the college years. Less than one-third (28 percent) of STEM-educated workers are working in a STEM job. The number of STEM degrees awarded in the United States is rising, but the number of STEM degrees awarded in China is rising at a greater pace (see Figure 9-2). Gehlhaus said that “foreign-born talent is the backbone of America’s innovation power,” but there is increased competition for talent. China has had talent programs for many years, and there is evidence that these programs have been effective.1 Without the right climate, policies, and infrastructure, there is no guarantee that foreign-born talent educated in the United States will want to stay, especially as China continues to invest in its innovation ecosystem and infrastructure. The United States is already losing top artificial intelligence researchers, 59 percent and 11 percent of whom were located in the United States and China, respectively, in 2019. In 2022, those numbers were 42 percent in the United States and 28 percent in China.
Gehlhaus said that the National Defense Education Act of 1958 was a “game changer” for education policy in the United States and called for an “NDEA 2.0.” Gehlhaus considers the CHIPS and Science Act (P.L. 117-167) to be a recent iteration of NDEA, as well as certain National Science Foundation initiatives. The key is to understand what combination of skills and competencies will be needed for the United States to maintain its competitive edge.
On research security, the Special Competitive Studies Project recommends taking a risk-based approach to decisions on whether international individuals should be allowed to work in the United States. Also, that it is possible to impose risk-based decisions that protect U.S. intellectual property without limiting needed inflows of talent. The project recommends denying visas to those with identified high-risk factors, regularly evaluating research security policy through an interagency process, and staying up to
___________________
1 Gehlhaus provided the following evidence that China’s talent programs have been effective: D. Shi, W. Liu, and Y. Wang. Has China’s Young Thousand Talents Program been Successful in recruiting and Nurturing Top Chinese Scientists? July 2022. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4043516.
SOURCE: Diana Gehlhaus, July 17, 2024.
date on trends in emerging and dual-use technologies so that decisions are technology informed.
The Special Competitive Studies Project also makes recommendations for increasing workforce competitiveness: making classrooms artificial intelligence–enabled by 2030, cultivating an advanced industry workforce, achieving high-skilled immigration reform by raising visa caps and reforming green card quotas, and creating a National Commission on Artificial Intelligence and the Future of Work that would champion consensus-based reform.
Norbert Holtkamp (Hoover Institution) discussed his June 2024 paper, co-authored with NSTSR members Thomas Mason and Anna Puglisi, “How to Create, and Sustain, R&D Leadership: A Blueprint for International Collaboration.”2 The premise of the paper is that an open and inclusive research system provides the fastest way to progress new discoveries and maintain our leadership. There is no doubt that the open, collaborative scientific environment has been compromised, there are threats faced by the United States, and we must act. However, because of U.S. response to these threats, funding organizations, universities, national labs, and principal investigators (PIs) spend significant time implementing risk-mitigating measures, assessing these measures, and training staff. This, in turn, has led to delays in achieving the primary objective of research: moving fast scientifically and staying ahead. Such delays allow our adversaries to catch up with us even faster. Enacting risk-mitigating measures also costs money, which diverts valuable research dollars away from performing research.
“Working with like-minded countries can protect our respective innovation bases, by developing an international agreement—including verification mechanisms—that would enable free collaborations while guarding against the actions of nations that do not adhere to those norms.”
Norbert Holtkamp
Hoover Institution
Enacting the recommendations of the most recent JASON report to review every proposal and understand every risk, Holtkamp said, will be
___________________
2 The paper is available at https://www.hoover.org/research/how-create-and-sustain-rd-leadership.
cumbersome. Further, achieving perfect security is not possible, so either way there will be risk.
Holtkamp said that these problems around science and security are not new and have been solved in other areas, for example, nuclear non-proliferation agreements. Such agreements allow for regulations to take place at a national level, rather than at an individual, university, or national lab level. Countries agree to the rules of the agreement and receive advantages in the form of access to technology and expertise.
To solve the challenges of research security, Holtkamp suggested that the United States assemble allies and partners with common values, write them down, and agree to abide by those values and the principles of international collaboration (and agree on an enforcement mechanism). A streamlined, risk-managed process among member countries, their institutions, and PIs would provide a kind of “TSA Pre-Check” lane for approval of international research collaborations. The incentive to stay in the agreement would be the ability to participate in international exchange and access to infrastructure, researchers, and data. Holtkamp said that such an arrangement would restore an open and fast research ecosystem and provide for an attractive work environment for the best and brightest from anywhere in the world.
Moler ended the panel presentations by sharing thoughts from absent NSTSR member Thomas Mason (Los Alamos National Laboratory). Mason, she said, strongly supports the “TSA Pre-Check” idea that Holtkamp presented and believes that when advancing U.S. S&T, “it’s all about the offense.”
DISCUSSION
Rebecca Keiser (U.S. National Science Foundation) said that conversations about a trusted international research network have taken place in international forums. When asked about levers available to reach privately funded researchers or other non-federally funded researchers, Holtkamp said that privately funded researchers would be affected to a lesser degree by the plan, but that it would allow publicly funded researchers to return to a mode in working with friendly countries that they are used to. Holtkamp’s co-author, Anna Puglisi, said that it would be possible to broaden the “TSA Pre-Check” idea to all sectors of U.S. S&T, but the paper represented an effort to lay out steps to begin to scope the idea, starting with the question: How do you enhance collaboration? By values, norms, standards? The
authors felt it was important to make the answers to these questions explicit, because so much is assumed about international collaboration.
John Gannon (formerly of the National Intelligence Council) expressed support for Droegemeier’s call for a national S&T security strategy, asking who might lead this effort. Droegemeier reiterated that the National Academies could convene a multisector, nationwide, politically independent effort. Droegemeier said that such a strategy “shouldn’t look like anything we’ve done before, because if it does, it isn’t going to be helpful.”







