National Science, Technology, and Security Roundtable Capstone: Proceedings of a Workshop (2025)
Chapter: 6 Funding Agency Responses
6
Funding Agency Responses
Rebecca Keiser (U.S. National Science Foundation [NSF]) provided an overview of research security at NSF. She defined research security using the definition from the National Security Presidential Memorandum—33 (NSPM-33) implementation guidance:1 “safeguarding the research enterprise against the misappropriation of research and development to the detriment of national or economic security, related violations of research integrity, and foreign government interference.” Keiser noted that the definition reflects the fact that research integrity and research security are deeply intertwined. An NSF “cell diagram” of research security (see Figure 6-1) places values at the center of the cell. Keiser described the cell membrane as porous, allowing for a system that can be both open and secure.
It is crucial to interface with international partners, Keiser said, citing G7 best practices2 indicating that openness and security are not contradictory but complementary and mutually reinforcing. Research security
___________________
1 Joint Committee on the Research Environment Subcommittee on Research Security, Guidance for Implementing National Security Presidential Memorandum 33 (NSPM-33) on National Security Strategy for United States Government-Supported Research and Development, January 2022, p. 24.
2 The G7 is an informal political and economic forum of seven of the world’s leading economies. For G7 best practices on research security, see G7 Security and Integrity of the Global Research Ecosystem Working Group. 2024. G7 Best Practices for Secure and Open Research. https://science.gc.ca/site/science/en/safeguarding-your-research/general-information-research-security/international-research-security-resources/g7-best-practices-secure-and-open-research.
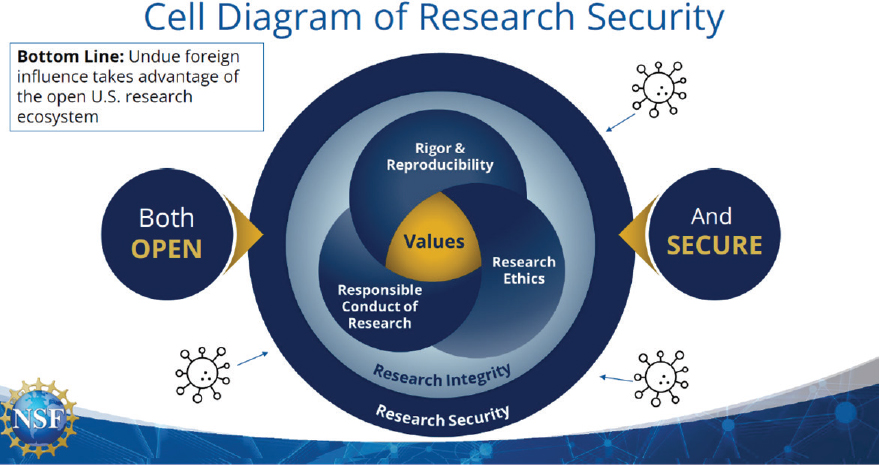
SOURCE: National Science Foundation, July 16, 2024.
needs to be considered at all stages, from fundamental research (including safeguarding researcher ideas, performing due diligence on funding sources, assessing potentially harmful end use, and differentiating international collaborations that are positive and productive from those that pose a threat to research security) to applied research (including safeguarding intellectual property, performing due diligence on sources of venture capital and investment, assessing potentially harmful end use, and vetting international transactions). Funders, research institutions, and researchers all have important roles to play in achieving research security.
Keiser highlighted NSF and other federal funding agency work:
- The White House Office of Science and Technology Policy issued guidance3 in July on requirements for research institutions receiving $50 million or more in federal R&D funding per year over the past 3 years. The guidance states that covered research institutions must establish research security programs that include cybersecurity, foreign travel security, research security training, and export control training. Keiser emphasized that federal agencies are working together to harmonize approaches to research security.
- The NSF, National Institutes of Health (NIH), Department of Defense (DOD), and Department of Energy (DOE) co-funded the development of research security training modules. The training modules, available on NSF’s website,4 are titled as follows: What is Research Security?; Disclosure; Manage and Mitigate Risk; and International Collaboration.
- NSF is setting up the SECURE (Safeguarding the Entire Community in the U.S. Research Ecosystem) Center to serve as a clearinghouse for information to empower the research community to identify and mitigate foreign interference that poses risks to the U.S. research enterprise. The SECURE Center will share information and reports on research security risks, provide training on research security to the science and engineering community, and serve as a bridge between the research community and federal
___________________
3 Office of Science and Technology Policy. 2024. Memorandum for the Heads of Federal Research Agencies. Guidelines for Research Security Programs at Covered Institutions, July 9, 2024. https://www.whitehouse.gov/wp-content/uploads/2024/07/OSTP-RSP-Guidelines-Memo.pdf.
4 National Science Foundation. n.d. Research Security Training. https://new.nsf.gov/research-security/training.
- funding agencies to strengthen cooperation on addressing research security concerns.5
- NSF is funding the Research on Research Security Program, which will identify and characterize attributes that distinguish research security from research integrity; improve understanding of the nature, scale, and scope of risks; provide insight into methods for identifying, mitigating, and preventing violations; and develop methodologies to assess the potential impact of threats on the U.S. economy, national security, and research enterprise.
- NSF is establishing a method for assessing research proposals for risk: TRUST (Trusted Research Using Safeguards and Transparency). The TRUST process is designed to assess whether research project personnel have active appointments or positions with entities on U.S. proscribed lists or are participating in malign foreign government talent recruitment programs. The process will also look for nondisclosure of information on appointments, activities, and sources of research support from the time after NSPM-33 implementation guidelines were released (January 2022) and will assess potential foreseeable national security applications of the research.
Harriet Kung (U.S. Department of Energy) shared the broad mission and science and technology (S&T) portfolio of DOE. The agency stewards 17 national laboratories and provides financial assistance across the full range of technology readiness levels, with awards ranging from grants to universities and loans to businesses. DOE must balance the need to protect its broad research enterprise, while promoting principled international collaborations and attracting and retaining the best and the brightest to its scientific programs. Kung displayed a timeline of research, technology, and economic security efforts at DOE (see Figure 6-2), demonstrating how DOE’s approach to research security policy has evolved across multiple administrations. While working groups on research security were first formed in 2016, recent White House guidance, statutory requirements, interagency processes, and DOE’s own continued evaluation of its research security policies has most recently led to the formalization of the Research, Technology, and Economic Security (RTES) Policy Working Group and the
___________________
5 The SECURE Center was launched on July 24, 2024. See https://new.nsf.gov/news/nsf-backed-secure-center-will-support-research. It will be led by the University of Washington with support from nine institutions of higher education.
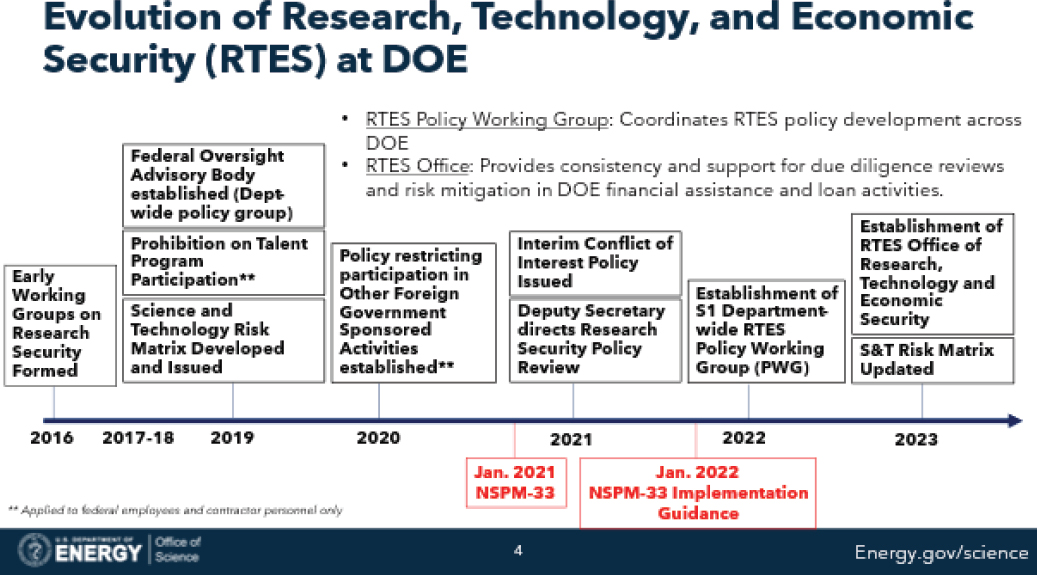
SOURCE: Department of Energy, July 16, 2024.
creation of the DOE RTES Office in 2023. The Office of Science works closely with the RTES Office to ensure that its due diligence reviews of research are transparent, do not create undue burden on researchers, and are risk informed by subject-matter experts. The Office of Science also participates in the annual update of the DOE S&T Risk Matrix,6 a tool for managing risks associated with critical and emerging research and technologies activities at the national laboratories.
Kung said that engaging leaders in the scientific community is essential to building trust and creating buy-in, and results in more effective policy implementation. Close working relationships with interagency partners are equally crucial for ensuring harmonization and reducing burden on the research community. At the same time, it is essential to maintain flexibility and transparency throughout policy development.
Important questions for DOE include the following:
- How can DOE strategically balance international engagement and research security?
- As due diligence risk reviews for fundamental research are implemented, how can DOE streamline the process so as to not affect timelines for awards?
- How can DOE develop nuanced criteria for assessing research risks that recognize the (sometimes blurry) boundaries between basic, applied, and more mature stages of R&D?
- How can we transition from a compliance culture to a culture of partnership with the research community?
- How can the interagency process support program managers, principal investigators (PIs), and administrative professionals in navigating the research security landscape?
Patricia Valdez (U.S. National Institutes of Health) discussed research security efforts at NIH. In 2016, the Federal Bureau of Investigation (FBI) alerted NIH of a peer reviewer sharing confidential grant applications with overseas colleagues. The FBI also raised concerns about foreign talent recruitment programs. NIH program staff began to flag foreign affiliations used as a primary affiliation, as well as foreign grants not previously disclosed to NIH on grant applications.
___________________
6 For more on the DOE’s S&T Risk Matrix, see https://www.directives.doe.gov/terms_definitions/science-and-technology-risk-matrix-s-t-risk-matrix.
Since 2018, NIH has received more than 650 allegations or notifications of undisclosed research support, undisclosed employment arrangements, diversion of intellectual property, financial conflicts of interest, and conflicts of commitment where an individual has committed to full-time employment in another country while simultaneously committing to employment in the United States.7 Valdez said that NIH works to ensure that allegations are investigated in a consistent manner.
The number of foreign interference allegations at NIH has significantly declined. In 2019, there were 184 allegations. In 2023, there were only 40. In the first part of 2024, NIH has received 11 allegations. This may be an indicator of increased awareness of research security issues, with individuals better understanding requirements and institutions more effectively communicating with researchers. Self-disclosures have increased. NIH views this as a positive because it shows that institutions are taking actions to ensure researchers follow research security procedures. Complete disclosures of the needed information in grant applications allows NIH to perform risk assessments more effectively.
In most cases, research institutions’ rules apply and administrative action takes place at the institutional level. NIH administrative actions include barring an individual from performing peer review, removing an individual from a grant, and efforts to recoup funds in cases where there is conflict of commitment.
NIH works closely with other federal agencies, including those funding research, and intelligence and law enforcement agencies. Valdez notes that NIH has spent a lot of time speaking with the FBI to provide a perspective into scientists’ working methods and to gain insight into intelligence and law enforcement.
“Researchers need to understand the risks that they may be taking when they enter into certain collaborations, and they should work with their institutions to mitigate the risks when possible.”
Patricia Valdez
National Institutes of Health
Valdez said that the agency works to avoid bias or discrimination based on ethnicity when conducting investigations of research security violations. Investigations look for contradictory informa-
___________________
7 For more data on NIH foreign interference cases, see https://grants.nih.gov/sites/default/files/Foreign-Interference-6-9-24-report.pdf and https://grants.nih.gov/policy-and-compliance/policy-topics/foreign-interference/fi-data.
tion and evidence that there was an intent to deceive, and not cases of, for example, forgetting to check a box on a grant form. The People’s Republic of China’s talent recruitment programs explicitly target individuals of certain ethnicities. Most, but not all, NIH cases involve China, and not all cases involve scientists who are ethnically Chinese. NIH is also seeing problematic behaviors from the governments of Russia and Iran, as well as from other countries. Transparency is important, and NIH publishes procedures, data, and case studies of research security violations on their website.8
Valdez said that collaboration, both domestic and international, is very important to solving the most pressing and perplexing health challenges, and that the exchange of knowledge with international partners is both an essential part of innovation and crucial for our global competitiveness. But “researchers need to understand the risks they may be taking when entering into certain collaborations, and they should work with their institutions to mitigate the risks when possible.” It is also important for NIH to engage with researchers to help them understand requirements and the reason for them. Valdez said that we can have robust international research collaborations and research security at the same time.
Bindu Nair (U.S. Department of Defense) said that DOD policies on research security look slightly different from other science-funding agencies’ policies, but that agencies are getting to the same place. DOD began its research security efforts by examining its purpose for funding basic research. One reason is that DOD would like to support new scientific discoveries because they may result in new opportunities for meeting its mission. DOD also does not want to be surprised technologically, and if the agency does not engage in collaborative research, including with those who are not allied partners, it will not be cognizant of new ideas in S&T. DOD always wants to have the advantage of knowledge, power, tools, or technique. Finally, DOD recognizes the important role research plays in developing the workforce for the scientific enterprise of the future.
“Same as NSF and DOE, [DOD] need[s] to have technically competent people making these highly complex, highly nuanced decisions about how to take risk. [And] we need people to be aware.”
Bindu Nair
Department of Defense
___________________
8 See https://grants.nih.gov/policy/foreign-interference.htm.
DOD has concluded it needs to make risk-based decisions about the research it funds by using technical program staff who have a full set of information. This requires competent, technical people able to make the highly nuanced decisions about risk. PIs and institutions must be engaged in that process. Nair said that a compliance, checkbox-based approach by PIs is not going to be productive. What DOD is seeking is not a regulatory-focused approach, but a knowledge-based approach to risk assessment. DOD is in the process of aligning their policies internally across the army, navy, air force, and DARPA (Defense Advanced Research Projects Agency). However, making risk-based decisions means there will not be absolute uniformity in the way that research funding decisions are made within these agencies.
DISCUSSION
Discussion began with consideration of when risk mitigation occurs in the agency review process. Keiser said that NSF’s TRUST process is being piloted on quantum technologies, and risk mitigations will be adopted after the review of projects on their scientific merit. Keiser feels strongly that input from merit review should be a factor in decisions about risk, because if a project has great merit, then a higher level of risk might be acceptable. Kung said that at DOE, the RTES Office reviews research solicitations prior to release. Once a proposal passes merit review, it may require additional review by DOE’s RTES Office. Valdez said that NIH’s regular risk assessments of research funding projects do not involve foreign interference reviews. Nair said that, at DOD, risk analysis happens after the selection of a proposal.
Jason Donovan (U.S. Department of State) said that he has heard concerns from European contacts about NIH’s “onerous” requirements related to the review of lab notebooks. Valdez said that the policy requirement is that any domestic institution with a subaward with a foreign institution must have a policy in place stating that lab notebooks at foreign institutions are subject to review upon request. This provides a means for institutions to access these documents more easily, because in the past there have been challenges associated with securing these materials.
Moderator Michael McQuade (Carnegie Mellon University) closed the session by acknowledging hard work over the 4 years of the roundtable’s existence by each of the agencies represented, in particular noting the individual efforts of Keiser, Kung, Nair, and Valdez within their
agencies and in collaboration with other agencies and with stakeholders outside of government. McQuade said that collaboration both among the agencies and between the agencies and other research security stakeholders is very good.









